
Session Initiation Protocol (SIP) is vulnerable to several attacks without the right security measures to protect the network. Compared to the traditional GSM network, in the IP Network, SIP works at the application layer. Thus it faces the dual threat of IP-network security and SIP protocol fraud issues.
Different types of protocols are used by the signaling networks such as SS7 or SIP, which are vulnerable to different types of fraudulent attacks. As a result, fraudsters take the advantage of the loopholes to break into subscriber privacy, prevent access to important services, and directly defraud mobile operators.
6 SIP/VoIP Fraud Attacks
CLI Spoofing and Robocalling
Hackers can impersonate a reliable organization by spoofing the caller id of victims. By this process, fraudsters are able to make a call to victims to seek their personal information such as account details, one-time passwords to indulge in cybercrime. For generating traffic, attackers use automated bots, which can bring high traffic loads.
Bypass Fraud
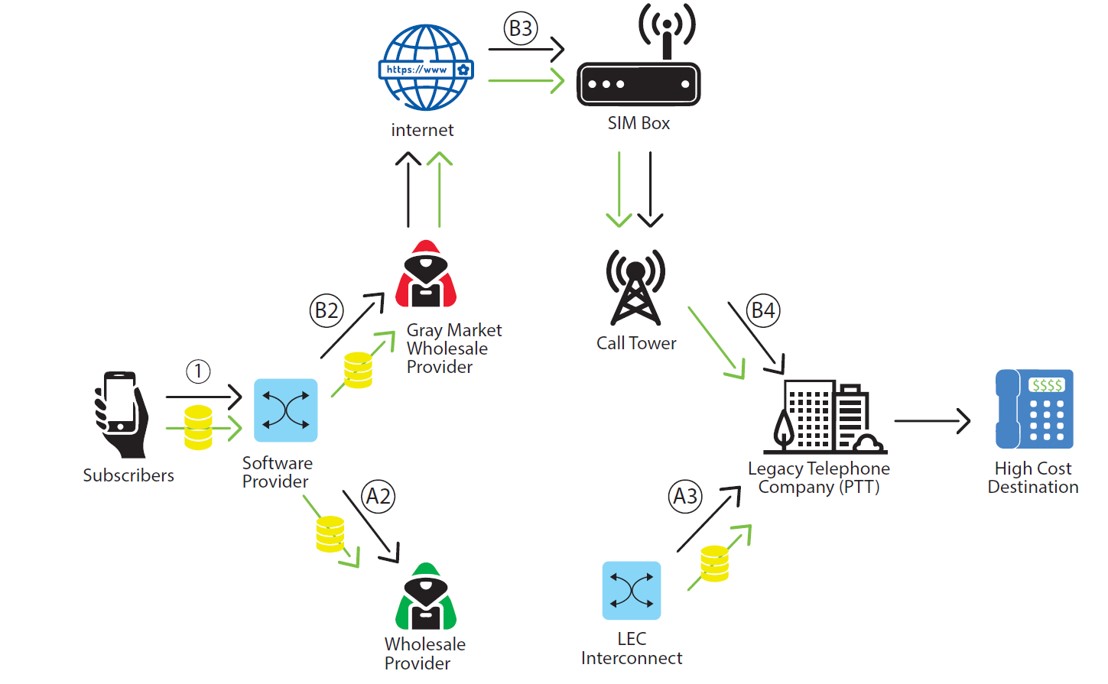
Bypass fraud is defined as the unauthorised insertion of traffic into another carrier’s network. Here the fraudsters make the international call appear as a low-cost domestic call thereby effectively bypassing the normal payment system for international calling.
Call Hijacking
Compared to traditional telephony networks, VoIP traffic is sent on the IP network without any kind of encryption. As there is no encryption involve in traffic transmission, session sniffing becomes easier.
Denial of Services (DoS)
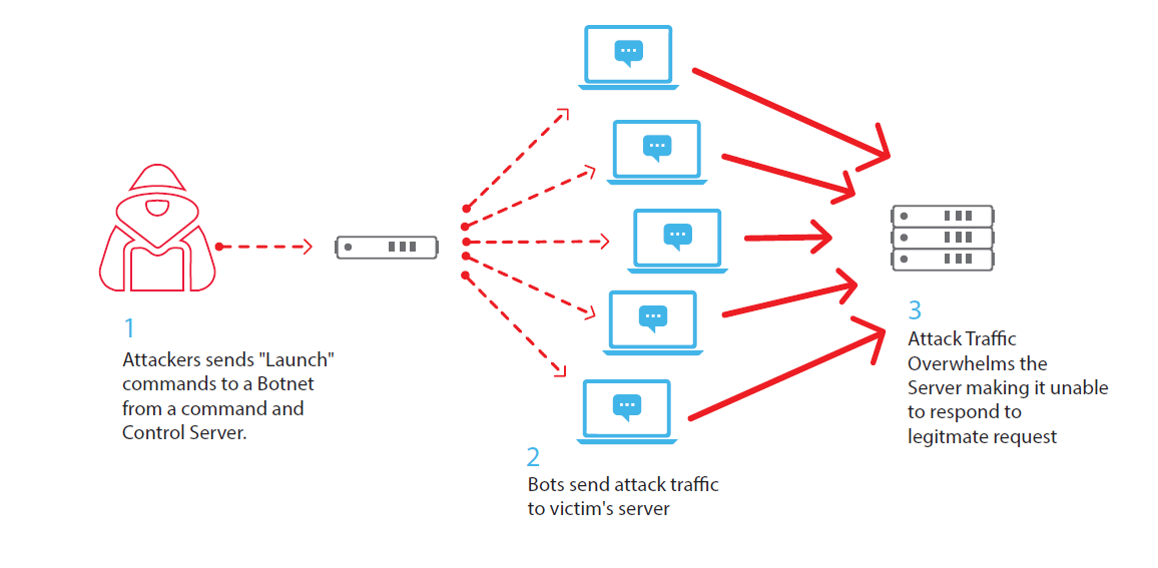
The Denial of Service attack is one of the biggest threats to VoIP Telephony. The main aim of the DDoS attack is to overload a system with too many requests so that the system is forced to shut down. In this process, the attackers move ahead to spoof their addresses and compromise other nodes (e.g., by Trojans).
SIP Registration Attack
SIP registration hijacking is a serious VoIP security issue. Before establishing a SIP session, there is a registration process, which can be hijacked by the attacker. In this attack, the attacker disables a user using Denial of Service and tries to register with his own IP address rather than the users IP address.
IP-PBX Hacking & IRSF
In this intrusion process, different types of hacking software are used to hack an IP PBX mainly for gaining access. Once the access has been attained, traffic pumping begins. Attackers also initiate calls to prime numbers through this process.
How Can Operators Minimize these Security Issues?
Operators and service providers can minimize these issues by employing Session border controllers to secure their VoIP infrastructure and control the access to VoIP services. SBC provides strong protection for the IP Communication infrastructure stopping frauds and service thefts. SBCs are designed to support various types of Sip interoperability, providing service assurance, and secure interconnection between VoIP networks.






















