
VoIP Network is becoming the most needed element in modern business communication. Although there is much cost-effectiveness and convenience associated with VoIP, it has its limitations when it comes to safety. As a communication provider, if you are using VoIP you will need a Session Border Controller (SBC) to mitigate the threats from network-based attacks. A VoIP Session Border Controller is also referred to as Class 4 Softswitch or Class 4 Switch.
Understanding VoIP Communication Networks
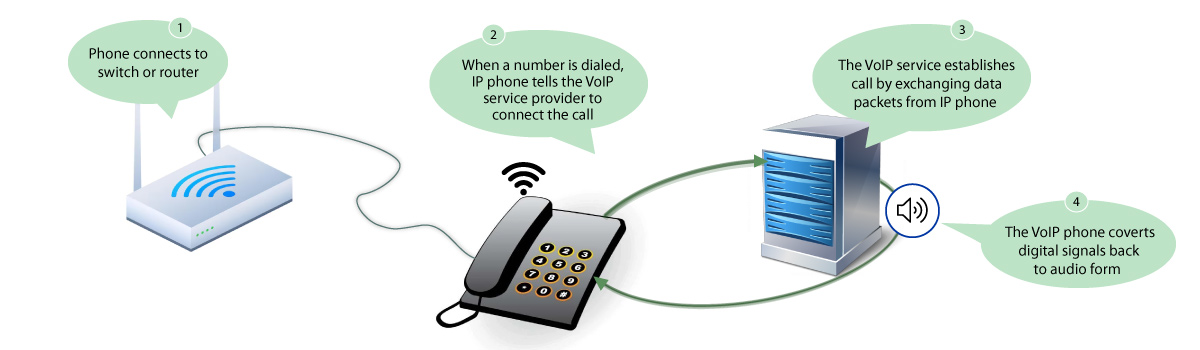 Undoubtedly, VoIP communication networks have dramatically transformed the way people connect, communicate, and conduct business. Eliminating the need for those traditional tele[phpone lines, VoIP enables voice and multimedia communication to happen over the internet cloud. It is a ground-breaking innovation that is not only cost-friendly and versatile but also efficient and effective. VoIP communication offers crystal clear voice quality, flawless video conferencing, and much more along with the ability to connect from virtually anywhere with an internet-enabled device. Below mentioned are some pointers for you to quickly take a grasp of VoIP technology:
Undoubtedly, VoIP communication networks have dramatically transformed the way people connect, communicate, and conduct business. Eliminating the need for those traditional tele[phpone lines, VoIP enables voice and multimedia communication to happen over the internet cloud. It is a ground-breaking innovation that is not only cost-friendly and versatile but also efficient and effective. VoIP communication offers crystal clear voice quality, flawless video conferencing, and much more along with the ability to connect from virtually anywhere with an internet-enabled device. Below mentioned are some pointers for you to quickly take a grasp of VoIP technology:
- VoIP technology enables voice communication over the internet rather than traditional phone lines by converting voice signals into data packets over IP networks
- This technology makes use of codecs to compress and decompress audio signals for efficient transmission
- Internet connectivity and bandwidth are two crucial components of VoIP
- Effective security measures are required to protect VoIP networks from unauthorized access and cyber threats
How do SBCs Secure a VoIP Communication Network?
Now, that we are clear with the understanding of VoIP networks, the next move is to understand the role of VoIP Session Border Controllers in the security of VoIP networks. Let’s take a look:
Prevention from DDoS Attacks
When it comes to security features of an SBC, Distributed denial-of-service (DDoS) protection holds prime importance. An SBC is placed at the edge of your communication network, which is connected to public networks resulting in higher exposure to DDoS attacks.
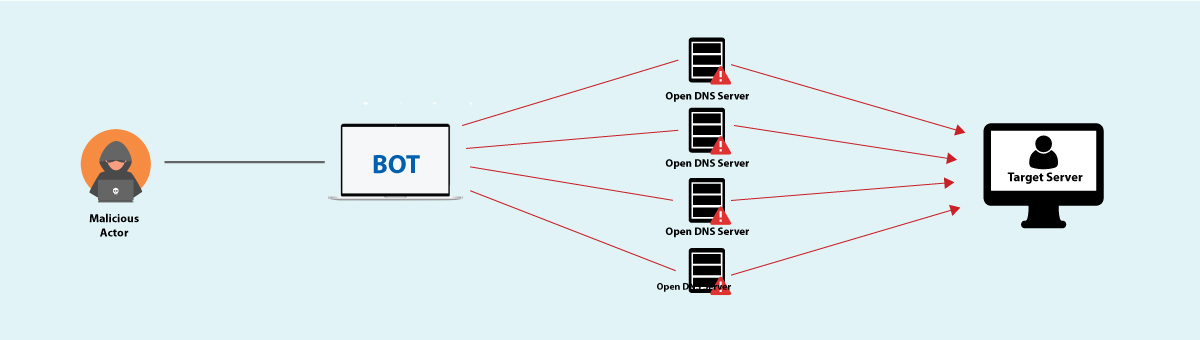 Attackers try to spoof the source addresses of the target to send requests to a Server Host (i.e. Reflector), that generates a reply toward the target victim which is much bigger than the request message, resulting in a large flood of traffic for the attack. Mentioning DDoS attacks, you should note that attackers use small packet sizes to remain undetected. A VoIP SBC accepts media packets only if they agree to a session negotiated via SIP/SDP signaling.
Attackers try to spoof the source addresses of the target to send requests to a Server Host (i.e. Reflector), that generates a reply toward the target victim which is much bigger than the request message, resulting in a large flood of traffic for the attack. Mentioning DDoS attacks, you should note that attackers use small packet sizes to remain undetected. A VoIP SBC accepts media packets only if they agree to a session negotiated via SIP/SDP signaling.
Quality of Service (QoS) Management
VoIP Session Border Controllers play an important role in ensuring the Quality of service management for communication networks. SBCs implement different types of techniques to prioritize and optimize traffic. With proper monitoring and regulation of the flow of voice and multimedia data, SBCs prevent congestion in the network and maintain seamless and smooth communication. Moreover, SBCs employ QoS policies that prioritize traffic to maintain QoS for critical applications. By providing Bandwidth Management and Call Admission Control policies, Session Border Controllers deliver an overall superior communication experience.
Traffic Policing
With a VoIP Session Border Controller deployed in your network, you can frame policies to receive calls only from your preferred list of users and reject them from the unauthorized user list. Traffic Policing identifies malicious attempts by attackers to flood the network. SBCs enforce traffic rules and regulations to monitor, validate and filter incoming calls. Whenever a call is instead by a user, SBC first validates the credentials and permissions of the user. In other words, it matches the user’s information with the list of authorized users. If it matches then it allows the user to proceed and connect, however, if it does not matches, then SBC denies access to it, thus preventing potential attacks and unauthorized access.
Topology Hiding with B2BUA
By performing the role of a back-to-back user agent (B2BUA), a VoIP Session Border Controller secures a core SIP network and application servers. It is an essential security feature that safeguards the internal network topology of a VoIP system from external threats and maintains the integrity of the network.
B2BUA is a system in which SIP calls are managed by a logical or virtual proxy set up for the call. With the help of B2BU, all signal and media traffic passes through the SBC hiding the topology, or architecture, of the network. This prevents the display of private IP addresses of servers making them less vulnerable to attack. With this, it prevents the attackers from gaining internal insights such as IP addresses, server locations, and other sensitive information that can be exploited.
Media and Signaling Encryption
An SBC is responsible for taking care of various types of media traffic along with processing signaling messages. In the process, SBC plays a dual role in securing the media flows along with the application of transcoding where servers and clients do not have a common codec.
Encryption and Decryption
Encryption is applied by an SBC to both the signaling session initiation protocol (SIP), and media (voice, video, IM, and so on).
A well-structured encryption system means that malicious agents can’t snoop on VoIP calls, media transfers, and other SIP-based communications. Here’s how encryption works:
- A VoIP call is initiated. The Session Border Controller intercepts the call signal and media traffic.
- Now, Encryption algorithms are applied by SBCs for converting voice and data packets into encoded form, making them unreadable and secure.
- Then the encrypted packets are transmitted over the IP network, thus protecting the call from potential threats.
The Decryption Process happens like this:
- The destination SBC performs decryption using cryptographic keys upon receiving the encrypted packets.
- The packets which are decrypted in the previous step are then reassembled and converted back to their original format.
- The decrypted media and signaling are then forwarded by the SBC to an appropriate destination.
SIP Protocol Validation
It is another important process of the SBCs that ensures the integrity of VoIP communications within a network. Here’s how it works:
- As the SIP Signaling messages traverse the SBC, it analyzes and validates the contents of the message.
- The SBC then examines the syntax and format with that of the SIP standards. It checks the headers, files, and the overall structure of the message.
- SBC also checks if the message complies with the relevant SIP version and specifications
- Then the SIP message is assessed for potential security vulnerabilities such as header manipulation, tampering, spoofing, etc.
- SBC then performs session control and routing to ensure that calls are routed to the right destinations required resources are available for sessions to happen
- It then converts SIP URIs to IP addresses and vice versa thus enabling seamless communication
- Then the network is evaluated for accommodating additional calls which is the Call Admission Control Process
Fraud Detection and Prevention
There are various ways in which SBCs detect and prevent fraud such as:
- SBCs perform Fraud Pattern recognition by continuously monitoring call patterns and usage behavior to detect any suspicious activities. It can be in the form of unusual call volumes and frequent call attempts.
- By implementing rate limiting, SBCs control call volumes and prevent call flooding that can lead to toll fraud attacks. This way SBCs protect against fraudulent activities.
- SBCs employ Intelligent call Blocking techniques based on some predefined criteria or rules to block calls. This is particularly helpful in the exploitation of premium rate numbers that lead to financial losses.
The Benefits of SBC in VoIP Security
Enhanced Network Security
Amongst the various benefits offered by SBCs, this is the primary one. Deploying a SBC in VoIP communication is just like hiring a gatekeeper. It protects the VoIP network from external threats which could be in the form of DoS attacks, eavesdropping, etc. VoIP Session Border Controllers enforce strict access control mechanisms that only allow authorized users inside the network and prevent unauthorized intrusions. By performing deep packet inspection, and monitoring the incoming and outgoing network traffic, SBCs mitigate potential security threats. With all these actions, the overall security of the VoIP network gets fortified.
Smooth Communication Experience
The incorporation of SBCs in the VoIP communication architecture ensures a seamless communication experience for the users. Session Border Controllers have the ability to manage Quality of Service i.e. QoS by prioritizing voice traffic, minimizing latency and packet loss. Through this SBCs deliver high call quality i.e. clear and uninterrupted voice calls in each and every session even when network traffic is at its peak. Moreover, the transcoding functionality of VoIP Session Border Controllers ensures that different audio codecs used by different devices making voice calls remain compatible with each other. This means that users can enjoy communicating effortlessly no matter the equipment they are using. Therefore, by optimizing the network performance, Session Border Controllers assure a superior communication experience for both businesses and end-users.
Regulatory Compliance
In today’s digital landscape, businesses using VoIP communication cannot escape the critical aspect of regulatory compliance. The role of SBCs in allowing businesses and organizations to adhere to relevant industry regulations and data protection laws is quite significant. SBCs enforce encryption of voice and multimedia which ensures that sensitive information is safe from unauthorized access. Here are some of the key aspects of regulatory compliance in SBCs:
- Data Privacy: The data handled and managed by SBCs is sensitive. By complying with data privacy regulations, SBCs ensure that sensitive user data is collected, processed, and stored in a secure and lawful way.
- Call Recording Compliance: Recording of calls is subjective to certain regulations. SBCs must provide the option to obtain consent from users for call recording and the features for secure recording and storage of calls.
- Emergency Services (E911): SBCs must adhere to regulations governing emergency services. Service providers must ensure that 911 calls are correctly routed to appropriate emergency call centers.
- Interoperability Standards: For interoperability to happen smoothly between various devices and service providers, SBCs should comply with IETF i.e. Internet Engineering Task Force and SIP Forum Standards.
- Quality of Service (QoS): It is important to prioritize voice traffic and maintain high-quality call connections by employing QoS standards.
- Call Routing: SBCs must adhere to call routing regulations such as number portability, and dialing plans, especially in case of international calls.
- Emergency Call Bypass: This is a critical mechanism to be implemented by SBCs in certain regions. It is to ensure that emergency calls are not blocked or delayed in situations of network congestion or outages.
- Fraud Prevention: SBCs must comply with regulatory measures that help in detecting and preventing fraudulent activities such as robocalls and toll fraud.
Flexibility and Scalability
The flexibility and scalability offered by VoIP session border controllers for VoIP networks are simply unprecedented. SBCs are adaptable to various VoIP deployments. So whether it is about integrating into existing communication infrastructure, or supporting different protocols and codecs, they fit in all. Here’s an explanation for better understanding:
- Protocol Support: Session Border Controllers can support multiple protocols such as SIP, H.323, RTP, and more which enables smooth interoperability.
- Protocol Conversion: By performing protocol conversion, SBCs ensure smooth communication between networks that use different types of VoIP protocols even in complex communication environments.
- Session Handling: SBCs have the capability to handle multiple sessions simultaneously thus ensuring smooth and stable communication even during peak traffic hours.
- Scalability: SBCs are designed to scale easily as the VoIP network grows. Businesses can add additional SBC instances or upgrade hardware resources to accommodate increased call traffic and user demands.
- Load Balancing: SBCs implement Load Balancing to smoothly distribute call traffic across multiple data centers. This results in enhanced network performance.
- High Availability (HA): SBCs can be configured in high-availability setups with redundant components and failover capabilities. Such configurations make sure that the communication remains uninterrupted in case of network or hardware failure.
Conclusion
In conclusion, the role of VoIP Session Border Controllers is pivotal in safeguarding VoIP networks from potential threats and vulnerabilities. We have explained in detail the various security features such as encryption, network topology hiding, Call Admission Control, etc. implemented by SBCs to enhance network security. It would be right to say that SBCs are the true ‘Guardians’ of today’s modern communication networks, providing a robust layer of protection to VoIP communication.
Is SBC necessary for VoIP networks with limited users?
Yes, SBCs are essential for VoIP networks no matter the number of users. It is a crucial component that secures and manages communication sessions as they happen between different types of networks.
Can SBCs protect against all types of VoIP attacks?
The threat landscape is ever-evolving and SBCs are effective in providing protection against several types of VoIP attacks like DDoS attacks, call eavesdropping, Toll-fraud attacks, etc.
Can SBCs be used for video conferencing security as well?
Yes, SBCs can be effectively used for video conferencing security as well. Modern-day SBCs not only provide security for VoIP communications but also video traffic and conferencing protocols.
Do SBCs require regular updates and maintenance?
Yes, regular updates and maintenance of SBCs are required to ensure optimal performance and security. Regular updates help in keeping the SBCs up-to-date with the latest standards. Maintenance activities ensure the smooth and reliable operation of the SBCs.
Read Also
SIP/VoIP Fraud Attacks: Why Operators Need a Reliable Solution?
Prevent Spoofed Robocalls with STIR/SHAKEN
Note- This post has been updated on 31-07-23.




























