
Today, our phones are nothing less than our lifelines. However, the constant bombardment of spoofed calls is not just an annoyance, rather it is a dangerous phenomenon that’s growing largely. According to the statistics, “In the U.S. as of August 2023, Americans have received 5.46 billion robocalls and each person receives almost 17 spam calls each day.” These figures reveal that scammers are constantly inventing new ways to attack users via spoofed robocalls. But how to prevent spoofing calls?
Remember what Benjamin Franklin once said, “An ounce of prevention is worth a pound of cure.” So, as the very first step, we must understand how spoofed robocalls happen, and different types of spoofing call scams, and of course, we will learn about some proven ways to prevent spoofing calls.
What is Phone Spoofing?
Phone spoofing is a technique where a caller deliberately falsifies the information transmitted to your caller ID display to disguise their identity. With phone spoofing, the caller can display a different phone number or name on your phone’s caller ID. This is done to make it appear as if the call is coming from a different source than it is. Many robocallers use spoofing to trick subscribers into answering their mobile phones. When the caller ID is changed by the robocaller, the call recipient sees a familiar number, it is known as spoofing.
I will help you understand Phone Spoofing with this example.
Alex is a corporate professional. One day, in the middle of an important project his phone rings. The call appears to be from a reputed bank where Alex holds one account. Upon answering, a recorded message informs Alex about a security breach in his account and urges him to “press 1” to speak to a live agent. Taken aback by the urgency of the situation, Alex presses 1, and the polite voice on the other end claims to be an employee from the bank. Alex is being asked to share his Social Security Number and other banking details to verify his identity.
Unknowingly, Alex shares his sensitive information, only to discover some unauthorized transactions in his bank account a few days later. Only then did he realize that he had fallen victim to a sophisticated phone spoofing attack.
The crux of the above illustration is –
A Spoofed Call will look like it is from a reliable organization or a phone number that’s similar to your subscriber. The main motive is to fetch the personal details like Bank or Credit Card information of the call recipient and indulge in cybercrime.
How Spoofing Works?
Phone Spoofing is accomplished by connecting the phone to a spoofing application. Such an application is software that replaces the original number of the caller with any other phone number using VoIP and PBX technology.
What are Spoofed Robocalls?
Before going deep into how to prevent spoofing calls, let’s understand what exactly is Robocall.
A robocall is a phone call that delivers pre-recorded messages through an automated dialer. It’s a common belief that robocalls are from telemarketers or even scammers, but they can also be used to deliver alerts and awareness. When Robocalls are combined with spoofing techniques, it becomes easier for scammers to get detected by the filtering systems. This makes it easy for the scammers to execute their fraudulent acts. Such attacks are also termed Caller ID Spoofing, Robocall Scams, Caller ID Fraud, Neighbor Spoofing, etc.
Robocalls are usually categorized in the following:
- Telemarketing
- Scams
- Payment Reminders
- Alerts
However, not all of these are a cause of concern as users will not get impacted by alerts or reminders. Only the spam calls generated by spammers affect the most.
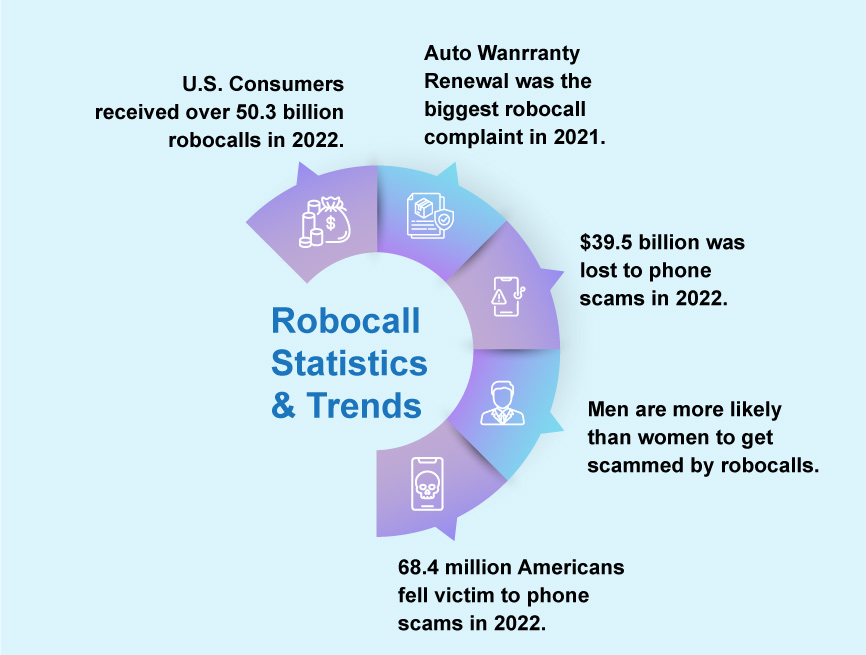
The latest report from Juniper Research, the foremost experts assessing emerging communications technologies, has found that mobile subscribers will lose $58 billion to fraudulent robocalls globally in 2023; a rise from $53 billion in 2022. The report predicts that fraudsters’ ability to innovate fraud methods will drive these losses to reach $70 billion globally by 2027. Source
Why do Phone Companies Allow Spoofing?
You need to understand that Spoofing is not always illegal. There are various valid use cases where spoofing is used by individuals and business organizations. Some scenarios are:
- Law Enforcement agencies like police often use phone spoofing to mask their original phone numbers to stay covert during investigations.
- Helpline services use phone spoofing to display a centralized phone number for outbound calls. This is done so that when customers call back, they dial the common number rather than the personal numbers of the agents.
So when is Phone Spoofing Illegal? Phone spoofing is unlawful when it is carried out with a malicious or fraudulent purpose.
Why is Phone Spoofing Dangerous?
As of 2023, robocalls increased the rate of fraud-enhanced money loss resulting in $47,908.75 billion across the world.
Phone Spoofing may not appear to be a serious threat, but it often leads to serious consequences. A scammer can execute a phone spoofing attack by pretending from a reputable organization. The scammer can manipulate the target to make them reveal their sensitive information. Such scams can easily turn out to be a thousand-dollar loss for the victims.
7 Types of Phone Spoofing and Robocall Scams
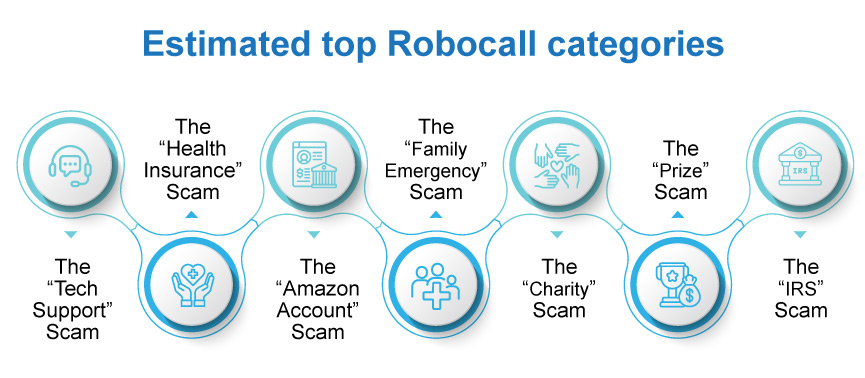
Scammers have numerous tactics to manipulate targets and fulfill their goals. The time of average robocall lasts for 45 seconds. Here are the top 7 phone spoofing and robocall attack methods used by scammers all around the world.
1. The “Tech Support” Scam
It’s a very common type of phone spoofing attack. Here, the scammer pretends to be from a tech support company. The target is informed that there is some serious technical issue with their computer and the tech support team needs remote access to fix the issue. Once the access is provided, the scammer installs malware or steals sensitive information from the computer system.
2. The “Health Insurance” Scam
Here the caller pretends to be from a well-known health insurance company. The scammer will say that your insurance policy needs to be renewed immediately by updating personal details. Once the details are shared, they use the information to commit various types of fraud.
3. The “Amazon Account” Scam
As the term suggests, in this type of scam the caller claims to be a representative from Amazon. The target is being told that there is some issue with their Amazon account and that they need to update their payment details. The motive behind these attacks is to fetch the credit card details from the target and use them for unauthorized transactions.
4. The “Family Emergency” Scam
Another common type of spoofing attack is where the caller pretends to be a family member, friend or loved one. The scammer will say that they are in serious trouble such as an accident and they need money immediately transferred to their account.
5. The “Charity” Scam
This type of scam tricks the target in a bit different way. They will pretend to be from a charity organization and will show gratitude for a donation that you made in the past. However, this is just to trick you into donating again.
6. The “Prize” Scam
In this type of scam, the caller informs the target that they have won a prize or a lottery in a lucky draw. The catch here is that the target needs to pay a certain amount of fee to get the prize.
7. The “IRS” Scam
In this type of scam, the caller claims to be from a statuary body such as the IRS and informs the target that they owe money. Often, the scammer uses a threatening tone to cause panic in the target and asks for an instant money transfer otherwise they will take legal action.
How to Tell if Your Phone is Spoofed ? 5 Red Flags
Now you may wonder about how you can spot caller ID spoofing on your phone. Watch out for these 5 red flags:
1. Non-familiar Phone Number
When a call arrives on your phone, the name displayed by the caller ID seems to be familiar but the associated phone number appears to be unknown, then it might be a Spoofed call.
2. Pre-recorded Voice Messages
When you answer a call, it plays a pre-recorded message that asks you to take an action by pressing a specific number for further instructions.
3. Need for Immediate Action
Creating a sense of urgency is a common tactic used in various types of attacks. In spoofed calls, the scammer impersonates someone familiar and demands immediate action, such as a transfer of money.
4. Asks for Sensitive Information
Spoofed calls often trick people into sharing their personal information such as their credit card information, net banking login credentials, etc. This information is used to blackmail the target or execute unauthorized transactions.
5. Display Name appears Familiar to a Known Contact
Suppose you have a friend ‘Sara Smith’ in your contacts and you receive a call from ‘Sarah Smith’. The display name is almost the same as your stored contact and maybe you might not be able to spot the difference at first glance.
How to Stop Someone from Spoofing Your Phone? Immediate Actions
Mobile Carriers often recommend certain guidelines that phone users can follow to stop spoofing attacks on their phones.
Report Suspicious Activities to Your Carrier
The majority of mobile carriers have dedicated support pages from where you can inform about any type of suspicious activities on your phone including calls.
Update Your Phone Call Security Settings
Often we ignore to customize security settings on our phones and go with the default settings, which might not be correct. Whether you have an iPhone or Android, you can limit incoming calls only from your contacts using your phone’s settings. This way you can stop scammers from using your phone number for spoofing.
Update your Voicemail Password
If scammers are using your phone number for spoofing, they might also have access to your voicemail messages. So it is a good idea to set a password or security PIN for your voicemail or update the existing one to prevent unauthorized access.
Get a New Phone Number
It’s probably the last resort. In case nothing works – you find that your phone number is heavily spoofed, and you are still bothered by scammers then changing your phone number is the best way to get out of that situation.
How to Prevent Spoofed Calls to Your Phone?
If you have been receiving spoofed calls on your phone recently, then you certainly need to take some immediate action to stop spoofed calls to your phone. Follow these 5 steps:
- Don’t Pick Calls From Unknown Numbers
- Do Not Call Back to Unknown Numbers
- Simply Block Robocalls from your Phone
- Block Phone Numbers that Appear Phishy
- Use a Phone Filter App to Block Unwanted Calls
- Initially Stay Silent When Receiving Calls from Unknown Numbers
How to Block Spoofed Calls on Your Device?
Block Unknown Numbers on iPhone
You can block caller ID spoofed calls on your iPhone by following these steps:
- From the Home Screen, open the Phone App. Now tap on Recents which will show your call history.
- Now Spot the phone number that you want to block. Select the info button next to the phone number.
- Upon scrolling down, you will find an option ‘Block this Caller’. Tap on this option and your iPhone will block this phone number for future incoming calls and messages.
Block Unknown Numbers on Android
You can easily block caller ID spoofed calls on your Android phone with the following steps:
- Open the Phone app from your mobile device and select Recents.
- Now Select a phone number that you want to block. Long press upon this number.
- A list of options will appear. Select ‘block/report spam’ option.
- Also, check the ‘Report call as spam’ box.
- Select Block and you are done.
How Can Mobile Carriers Guard Against Spoofing?
So what options do carriers have to prevent this Robocalling? The Federal Communications Commission (FCC) has notified carriers to implement call authentication measures by adopting STIR/SHAKEN standards in the United States. U.S. consumers receive approximately 4 billion robocalls per month, according to private analyses.

Implementing STIR/SHAKEN with a Session Border Controller
Deploying an SBC is one of the most effective measures to mitigate these fraudulent calls through the STIR/SHAKEN framework.
What is STIR/SHAKEN?
The Secure Telephony Identity Revisited (STIR) framework is developed by the Internet Engineering Taskforce (IETF) and defines a signature to verify the calling number and its transmission on SIP.
On the other hand Signature Based Handling of Asserted Information Using toKENs (SHAKEN) is another framework created to provide an application profile for service providers applying STIR.
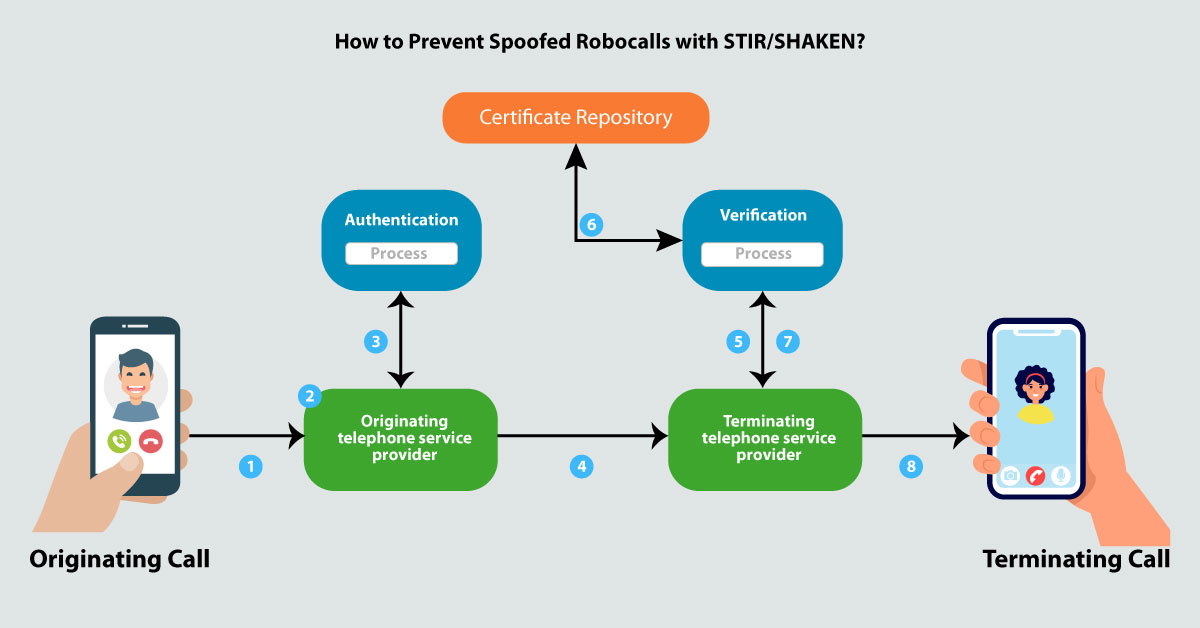
In simple terms, the call-originating carriers will sign the caller IDs as legitimate and validated by other carriers before they reach the users.
There are several components of STIR/SHAKEN but the main element is the SIP headers of each originating call that will carry an encrypted token validating the sender and the caller ID authenticity which can be decrypted and confirmed at the terminating end.
With an SBC, service providers can combat spoofed robocalls through caller ID authentication. STIR/SHAKEN solution in a Session Border Controller aids in the authentication, signing, and verification of calls.
A Common Deployment Architecture for SHAKEN
- Calls are signed by the interconnecting Session Border Controller as they leave the originating carrier’s network
- The interconnect SBC verifies the Call as it enters the terminating carrier’s network
SBC is one of the most robust solutions in the industry to prevent unwanted robocalling. Communication providers are rapidly adopting this solution in their network to not only prevent robocalling but also various types of telecom frauds.
REVE SBC & STIR/SHAKEN: Combatting Spoofed Robocalls

REVE’s Session Border Controller is equipped with STIR/SHAKEN protocols and serves as a critical tool for communication service providers in safeguarding their networks against spoofed calls and robocalls. REVE SBC establishes a framework of trust and authenticity, fortifying the integrity of telecommunication systems while adhering to regulatory standards. Take advantage of the free demo to test how REVE SBC integrates STIR and SHAKEN protocols to offer a robust defense to stop spoofed robocalls.
Read Also
SIP/VoIP Fraud Attacks: Why Operators Need a Reliable Solution?
Importance of a Session Border Controller in SIP Trunking
Note: This post has been updated with the latest information on 19-12-23.




























