
In today’s unified communication environment, a Session Border Controller (SBC) plays a major role in security, interoperability, and transcoding. This SBC software is highly capable to automate the entire process and do the call translations with the help of built-in interoperability features. The advanced transcoding capabilities of an SBC allows it to execute the audio translation process seamlessly.
With the growing network security threats, there is a constant requirement to upgrade the products, hence session border controller vendors nowadays constantly try to add new features to make this solution more robust and effective. In this blog, we have added detailed information about what is a session border controller and how this solution proves useful for communication service providers as well as for enterprises.
What is a Session Border Controller (SBC)?
Session Border Controller is a network element, which is used to control real-time communication calls or sessions. An SBC Software helps secure the important parts of a business’s communication network infrastructure. It protects and governs the IP communication flows, or in simplified terms, governs how calls are initiated, conducted, and terminated over the VoIP network. Furthermore, Session Border Controllers secures enterprises and service provider’s RTC infrastructure.
“Session” in SBC means communication that takes place between the caller and the receiver. There are media streams in the calls which work to carry the audio and video elements of the call along with other data. A Session border controller works to manage the data flows of all the sessions.
The term ‘border’ indicates a point of separation between each part of the network. In organizations, the Session Border Controller works to manage the flow of data across these borders.
The final letter C stands for ‘controller’. It means the control of SBC on the data streams that have sessions within it. A dedicated SBC also works to execute data conversion facilities and measurement, access control for all controlled calls.
Types of Session Border Controller
- Hardware: Dedicated physical equipment installed on your business’s premises.
- Software: A virtual Session Border Controller software running on your server.
- Cloud: A cloud-based Session Border Controller VoIP solution for your business.
Understanding A Carrier-Grade Session Border Controller
The 4 points which make an SBC Software unique are Performance, Scalability, Reliability and Redundancy. Powerful and robust with high capacity and redundancy, these solutions are not only able to handle the average number of calls coming through the system simultaneously but also to can handle peak calls easily.
The performance, scalability, and resiliency of SBC are evaluated through the following factors:
- Session Capacity & Scalability: To know about the capacity, look for the number of Concurrent Calls supported. How many concurrent calls is it rated for? How can this match the network’s usage patterns? And also if there is an increase in usage and it exceeds the capacity of the SBC, can it be upgraded or not?
- CPU Utilization: CPU utilization during peak periods should be able to handle plenty of overhead.
- Registration Capacity: To understand this, you need to look for the number of clients the SBC can register in a fixed period? This is also known as registration storms. When numerous users are connecting at once, the SBC should be capable of handle it.
How does a Session Border Controller work?
An SBC is a wall or a point of demarcation between your enterprise network and the service provider’s network (the internet). It secures and controls a SIP network by admitting (or not admitting) and directing communications between the internal and external world, such as a VoIP call between two phones or a video collaboration between multiple devices.
SBCs deployed at the network perimeter (or border as the name suggests). So that they can control and secure real-time communication sessions for both enterprises and service providers.
Early models of Session Border Controllers were used to protect and control the networks of VoIP service providers, but today it’s used to regulate all kinds of real-time communications in modern businesses. That includes phone calls, instant messaging, video and audio collaboration, and also desktop sharing. Today enterprise Session Border Controllers are also quite popular to provide a robust secure environment.
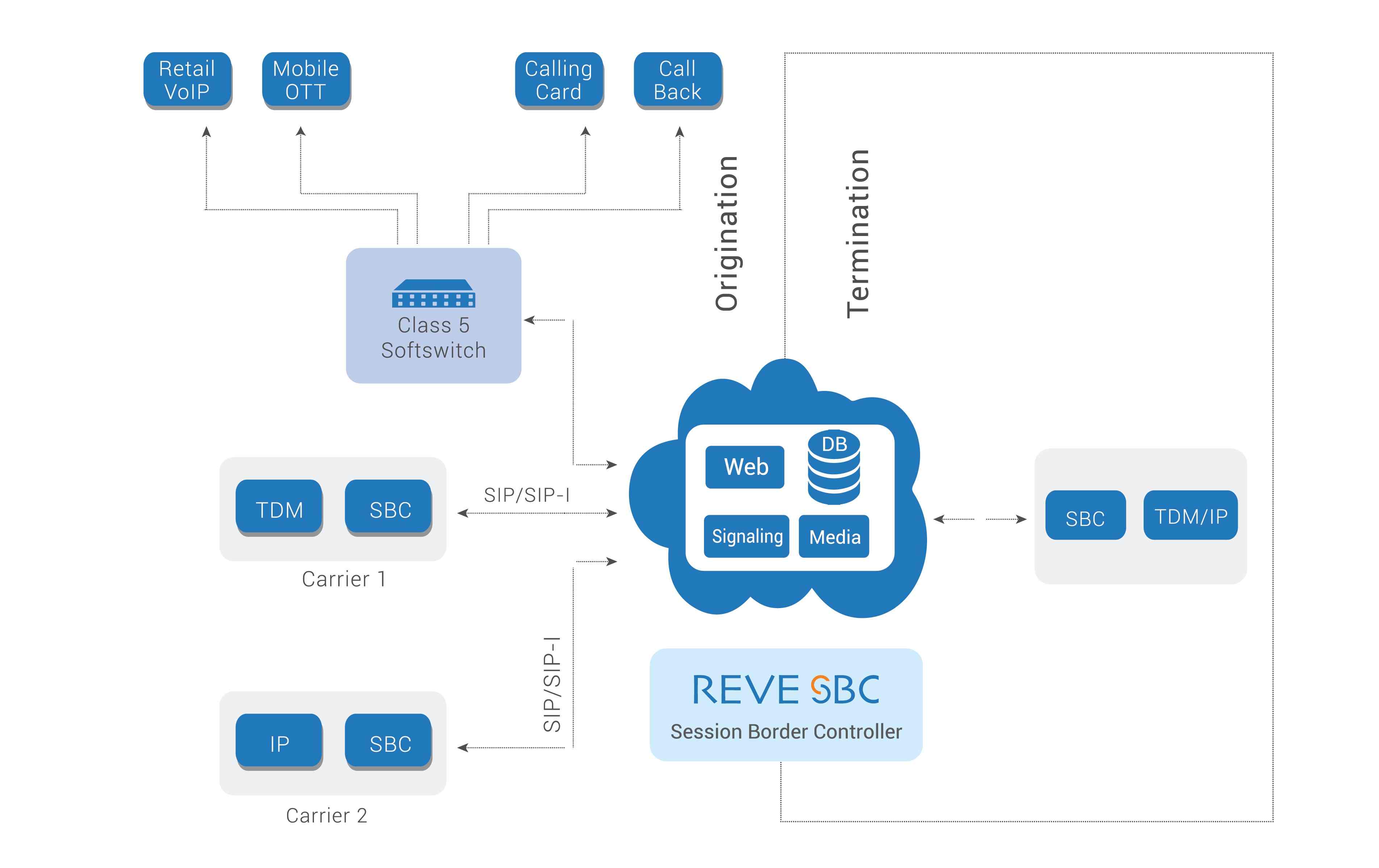
Functions of A Session Border Controller
Telecom carriers use SBC for signal translation and security. In a VoIP network, the role of this software is to implement control over media streams and signalling. These are some very basic functions. application of a Session Border Controller might vary for each organization.
Let us look into some of the core functions of an SBC:
Securing The RTC Network
A Session Border Controller protects real-time communications from threats such as toll fraud, DoS attacks (Denial of Service), and spoofing by acting as a Back-to-Back User Agent (B2BUA) and hiding network topology. SBC software also enables encryption of signalling and media to prevent communication tampering. Further, call admission control & dynamic blacklisting of rogue endpoints avoids toll fraud and telephony DoS. Watch this webinar to know more How to Secure Your Network with An SBC
Enabling SIP Trunking
As mentioned above, SBC is a demarcation or termination point of the SIP trunk connection in your communications network. It’s more like a SIP firewall that also includes an array of value‐added services like signalling and media inter-working, intelligent routing control, resiliency, and high quality of service between different network devices.
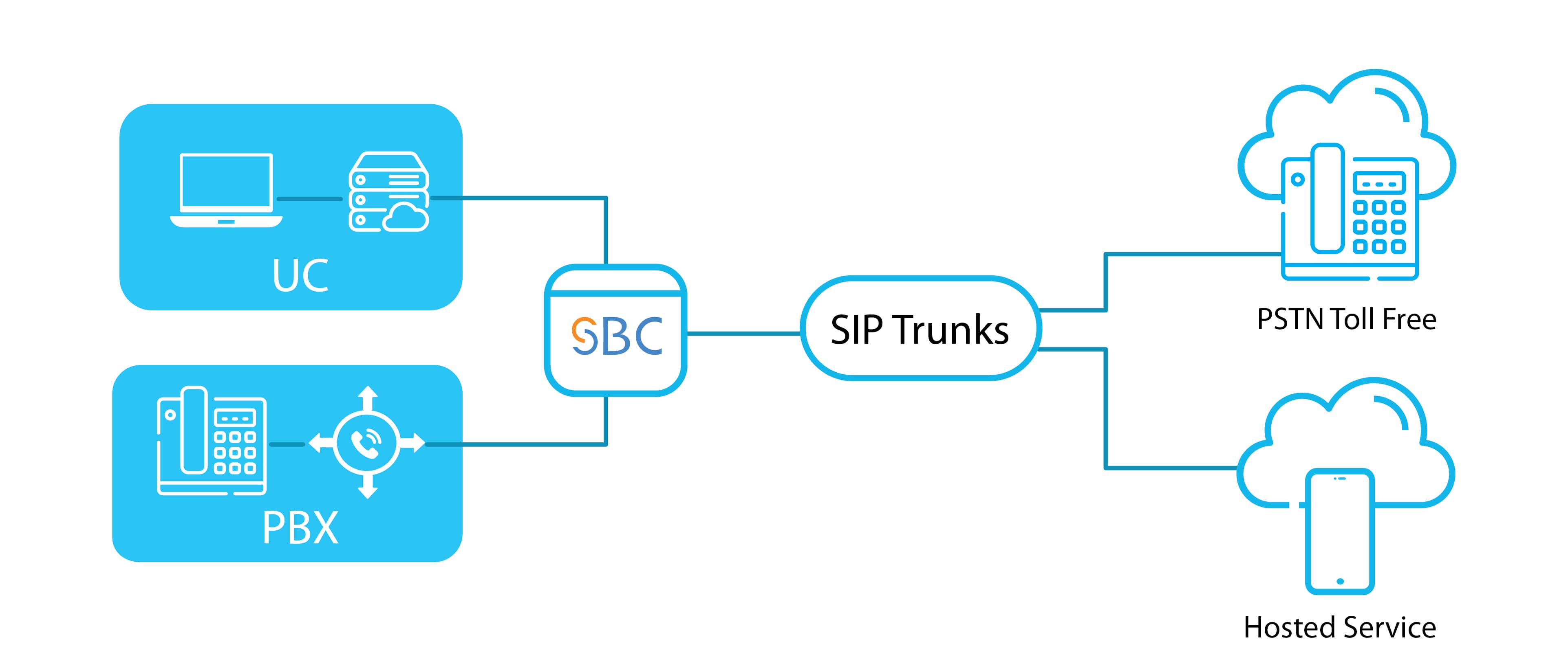
The Session Border Controller looks at each session crossing between the internal enterprise network and external ITSP network. Thereafter it determines where to route the session and what priority is necessary to assign to the session when the network is busy.
The function also includes determining how much bandwidth is necessary for a session. The network utilization and the policies established for the network determines the amount of bandwidth necessary.
In addition to the others, the software performs SIP interworking. This allows devices that subtly seek different variants of SIP to communicate with each other effectively and efficiently.
Here are some ways in which SBC helps SIP Trunking:
- Helps to bypass the security roadblocks
- It allows the centralization of architecture and process
- It smoothens the functional differences and adds essential features
- Acts as a “bridge”
- It also provides ongoing operational metrics and monitoring
Interconnecting Networks & Protocols
SBC smoothly performs the inter-working and interconnecting tasks, such as dealing with SIP variants and translating protocols, between different networks and the protocols running over them. SIP has a lot of variants; an SBC software can translate these variants between devices so that the calls get through with all their features intact.
Session Admission Control
SBC performs session admission control which means it inspects and sees who should be allowed to access the network and who should not. To perform this task, it creates three lists: whitelists, blacklists and grey lists. With this task, it maintains the QoS (Quality of Service) on the network.
The software reserves the resources of the service provider’s network to handle calls being set up. There are various ways for the SBC to achieve this. It also reserves “signalling bandwidth” for emergency services calls and prioritizes the emergency calls appropriately which is allowing them through Call Admission Control, while other calls are being rejected.
Intelligent Policy & Routing Controls
A policy has a set of rules that defines how the SBC treats different kinds of VoIP events. It allows control of the VoIP signalling and media at an application level. We can set multiple policies on a single SBC.
Advanced Routing includes a wide range of routing all of which have a similar end goal that is cost-efficient quality service. Source and Destination based Routing, Loss Less Routing and Least Cost Routing, Percentage Based Routing are some types of advanced routing.
5 Major Security Concerns Addressed:
1- Defends against Malicious attacks:
DOS or DDOS attacks are a serious annoyance. These attacks flood the network with bad traffic which degrades the quality of voice and video. Session Border Controllers help to separate voice traffic from general traffic and mitigate the maliciousness of attacks. In addition to this, the in-built firewall allows the voice to pass through while dropping other traffic. This, in turn, minimizes the impact of DOS attacks.
2- Toll Fraud Protection:
Toll Fraud is where hackers hack into a business VoIP system and make calls and the company has to pay the bills. The increasing amount of Toll Frauds all over the world is a major concern. Configuring the SBC to disable all sources of secondary dial tones will help to prevent them.
3- Encryption:
Encryption of signaling and media traffic is one of the best ways to secure real-time communications. Session Border Controllers use Transport Layer Security to secure the signaling traffic and render it invisible to hackers.
4- Topology Hiding:
Recipients of VoIP messages can understand the topology of the network and also the route it takes to pass between two networks. Session Border Controllers can protect against this using the feature “topology hiding”. This feature removes sensitive information by rewriting the VoIP headers in the signaling messages that they send across the network boundary. SBCs achieve this by acting as B2BUAs. They terminate the VoIP signaling that they receive from within the private network and signal a new call to the public network.
5- Traffic Management:
Using this feature a Session Border Controller limits the number of active sessions at a time. The network operator can configure the SBC with rate limits to control the rate at which all VoIP signaling messages is allowed to enter or leave the network. Separate limits can be applied based on per session, per port, per subscriber, per network, per group of subscribers, and more. It helps to maintain call quality along with a big call volume.
Difference between an SBC and a Firewall
It is important to understand the differences between a carrier-grade Session Border Controller and a firewall. SBC is designed to manage and control real-time voice and video communications sessions. While the conventional security product, the function of the firewall is to block or allow data communications flows.
Most business owners, who are not much into the concept wonder if an SBC is similar to a firewall as they are not must sure about their exact requirements. Once, you have set up your company, you need to apply all types of security protocols. So what type of solution do you need? Is it a Firewall or an SBC? Let’s discuss each in detail.
Firewall
It is possible to divide a computer network into seven layers. The Open System Interconnection (OSI) separates these layers. From the frame to the network segment, the Firewall works to control up to layer 3 and 4. In a typical VoIP network, Signalling and Media are two types of streams.
To execute signalling, a firewall has to open only a couple of ports but the opening of thousands of ports is needed for media exchange. Organizations thereby add firewalls into the DMZ but that does not prove much effective.
Firewalls prevent unwanted traffic from entering or leaving, a network by performing basic packet filtering. Firewalls filter packets only by examining packet headers and do not understand the payload of the packets. Hence, they do not filter out all types of unwanted traffic.
Session Border Controller
On the other hand, a Session Border Controller is capable of working in the 7th layer. Based on Signalling, an SBC controls port access. In many situations, private IP addresses are rewritten by SIP headers, which plays effectively in the case of internal to external routing migration.
Therefore, the main difference between an SBC and a firewall lies in the underlying architecture. The SIP firewall is implemented as a SIP proxy server. This is responsible for relaying and controlling SIP signalling information. However, this is not actively involved in the audio and video streams or the RTP media path.
On the other hand, the implementation of Session Border Controller takes place as a B2BUA (back-to-back user agent). It actively processes both the signalling and media paths. B2BUA terminates a session from one SIP entity (the caller) and simultaneously establishes a separate session with another SIP entity (the recipient).
This enables the SBC to inspect and manipulate the contents of the entire session. And thereafter, it can enforce security policies for efficiently managing enterprise communications. Understanding the differences between a firewall and SBC will help you select the right one for your business.
Can a session border controller be deployed in the cloud?
Yes, Cloud-based SBCs are quite popular due to the numerous benefits they offer including such as more flexibility and scalability, cost-effectiveness, and reliability as compared to on-premise SBCs.
How does SBC Protect against Denial-of-Service (DOS) Attacks?
SBCs act as a first line of defense against DoS attacks by implementing various security mechanisms such as rate limiting, signaling protection, media protection, and traffic rerouting to ensure service availability.
Can a session border controller be used with SIP Trunking?
Yes, in fact, an SBC act as a key element of modern SIP trunking as it addresses the associated security challenges by monitoring all session crossing between the internal enterprise network and external ITSP network and preventing incoming threats such as DDoS Attacks, Premium Number Fraud, Missed Call Fraud, etc.
Does SBC support Fraud Detection and Monitoring?
Yes, SBCs support fraud detection and monitoring by implementing various security policies such as monitoring traffic patterns, blacklisting, Call Rate Limiting, and preventing unauthorized access to the VoIP networks.
How to Secure Your Network with an SBC?
SBCs can help secure a network by preventing access to unauthorized users and implementing a range of security features such as Traffic Policing, DoS and DDoS attack detection and Blocking, Encryption, Access Control, etc.
Read Also
Frequently Asked Questions when Buying a Session Border Controller
The Importance of a Virtual Session Border Controller
Note: This Blog is updated with the latest information on 7th July 2021





























Pingback: Why Communication Service Providers Need a Session Border Controller()
Pingback: Role of Session Border Controller in Real-Time Communication Network – REVE Systems()